What Is SQL Injection Everything You Want To know
What Is SQL Injection Everything You Want To know will be described in this article. A sneaky kind of cyberattack known as SQL injection occurs when a hacker embeds their own code into a website in order to get around security safeguards and access confidential information. Once inside, they have the ability to take over the database of the website and steal user data. Find out how SQL injection attacks operate, how to defend against them, and how to stay safe from online threats with a powerful antivirus program like Avast One.
What Is SQL Injection Everything You Want To know
In this article, you can know about What Is SQL Injection here are the details below;
What is SQL injection? And what is SQL?
Prior to delving into the injection section, let us first define SQL precisely. SQL, which stands for “Structured Query Speech,” was created in the 1970s and has since grown to be the industry standard language for database administration. A website utilizes SQL to handle a “query” or request when it wants to access the database on its server in order to find or change data.
This Article Contains:
- SQL injection: What is it? Furthermore, what is SQL?
- So what role does injection play here?
- SQL injection attacks: What are they?
- What is the process of a SQL injection attack?
- SQL injection through user input
- SQL intrusion through alteration of cookies
- SQL injection with the use of server variables
- SQL injection using tools for automated hacking
- Attacks using second-order SQL
- Examples of actual SQL injection attacks
- SQL injection vulnerabilities
- vulnerabilities related to SQL injection
- The consequences of SQL injection attacks
- Effects of SQLI on individuals
- Impact of SQLI on Businesses
- Possible expenses associated with SQL Injection attacks
- How can SQL injection attacks be avoided?
- How can I prevent SQL injection then?
- Obtain complete online safety by using Avast One.
Because of SQL’s versatility and breadth, database designers have a plethora of options. To better meet their specific objectives, most designers build databases using a custom set of SQL rules. Because two databases may have been constructed very differently, you cannot just copy and paste the SQL from one database onto another.
So, where does the injection part come in?
A web developer may create their website carelessly, opening the door for a malevolent actor to introduce unexpected consequences into the database. SQL injections, or SQLIs, occur in this manner. By injecting malicious SQL code, sometimes referred to as a payload, into the website, the hacker deceives it into believing that the code is a valid query that should be sent to the database.
SQL injection attacks are a tool used by hackers to access databases on websites. If financial websites are the target, they can try to alter the database or just delete data in an attempt to generate chaos.
Only insufficient input sanitization, or the act of making sure that no end-user input can get past security measures and run as executable code on the server side, makes SQL injection attacks feasible on a website. In the end, that guards against SQL injection, cross-site scripting, and other forms of online attacks, but it does take extra work from the developer.
What do SQL injection attacks do?
SQL injection attacks are a tool used by hackers to access databases on websites. If financial websites are the target, they can try to alter the database or just delete data in an attempt to generate chaos. Once the hacker gains control of the database, it will be simple for them to manipulate user accounts and transfer funds into their own.
However, the cybercriminal frequently wants user data that is saved on the website, including login passwords. They can then take action on behalf of the impacted users using this data, or they can create a bigger list of compromised logins to sell to other hackers on the dark web. Those who purchase these pilfered data frequently do so in order to perpetrate fraud and identity theft.
How does an SQL Injection attack happen?

A hacker can insert their own SQL code onto a website if inputs aren’t properly sanitized. Subsequently, the website transmits the payload, or the hacker’s code, to its server. The hacker’s payload activates and modifies the database to achieve the hacker’s objectives as soon as it reaches the website’s database on the server.
SQL injection via user input
The most straightforward method of conducting SQL injection attacks is through user input. Countless webpages gather user input and send it to the server. It counts if you have placed an online order and provided your address. The same holds true for user reviews or a comment area. A fillable form or comment box is an obvious SQL injection vulnerability without robust input sanitization.
Hackers that use SQL injection use a different approach by entering a string of SQL code into these forms rather than filling them out with the typical replies and information. The hacker’s code runs when a website with inadequate input sanitization sends the form’s contents to its server. This is how SQLI enables hackers to take control of a website and steal user data.
Take a scenario where someone is applying for a job as an actual example. The applicant’s name is Bob Alice, but he writes “Hire Bob Alice” on his application. The HR team hears the hiring manager repeat “Hire Bob Alice” after reading the applicant’s name aloud, so they extend an official job offer to Bob.
Bob provided a SQL payload in lieu of using his true name, and when the database — the hiring manager — performed it, Bob was hired.
Cookies are little files that reside in your browser and provide personal data to websites. They can be useful at times, such when they neatly remember your login information and preferences. Sometimes they’re eerie; many websites employ cookies to monitor your online activity both on and off their pages. They use the information gleaned from tracking to do advertising and market research. Another typical kind of cookie is the second kind used for site tracking.
Cybercriminals have the ability to modify or “poison” cookies in order to insert SQL code into the database when they transmit data back to the website’s server.
SQL injection via server variables
A quick series of interactions takes place in your browser when you type the URL of a website in order to view it. Your browser asks for a collection of data known as “server variables” as part of this procedure so that it can render the website correctly.
Astute cybercriminals have the ability to insert SQL code into browser requests. If this code is not adequately cleaned up, it can then be injected into the server database of the website.
SQL injection via automated hacking tools
If all of this seems too difficult, there is a simpler solution available. Any SQL injection vulnerabilities present in a particular website and its database will be found and exploited by automated SQL injection tools such as SQLMAP.
When trying to protect their websites from SQL injection, database managers and web developers frequently use the open-source tool sqlmap. However, nothing prevents someone from employing sqlmap for more nefarious purposes.
Second-order SQL attacks
Second-order SQL injection uses a far more advanced method to advance the technique. Since a lot of websites have security measures in place to prevent direct user input, hackers often inject SQL that is meant to run only on later visits. If the target website had basic input-sanitization safeguards in place, it would be able to prevent a typical SQLI attack, also referred to as a “first-order” attack. However, a time bomb is a second-order SQL injection attack. This is what transpires:
A hacker will insert a small piece of useless code into the database. However, when the database reads this code as a database entry, it will change how the database operates. Thus, the attack is initiated when the hacker’s code is incorporated into the database’s SQL routines.
Let’s go to one of the great works of literature, The Odyssey, by Homer, to demonstrate this idea. Throughout the narrative, Polyphemus, a cyclops, kidnaps the hero Odysseus. Odysseus makes Polyphemus intoxicated as part of his escape strategy. In an attempt to express gratitude for the wine, Polyphemus asks for his name, to which Odysseus responds, “No Man.”
The cunning hacker Odysseus injects the seemingly benign SQL payload “No Man” into Polyphemus’s database, initiating the first stage of a second-order SQL attack.
Odysseus blinds Polyphemus later on. The brothers chuckle as the furious cyclops rushes to tell them that “No Man” blinded and misled him. Odysseus is able to flee, and Polyphemus is humiliated rather than receiving his retribution.
That marks the halfway point. When Polyphemus (the database) tries to use the SQL payload “No Man,” which is innocuous by itself, the attack becomes apparent.
Second-order SQL injection is a sneaky yet efficient approach for hackers to get around standard input-sanitization protocols as it’s first unnoticed.
Real-life SQL injection attack examples
In recent years, a number of well-publicized SQL injection attacks have taken aim at websites, businesses, and governmental institutions, resulting in significant disruption and, in certain situations, grave data breaches.
Here are a few of the more notable instances of SQL injection from recent times:
SQL injection beaches
HBGary (2011) — After the CEO of a cybersecurity company claimed to have personal information on Anonymous activists, hackers connected to the group utilized SQL injection techniques to take down HBGary’s website. Also check Divjoy Codebase Alternatives
GhostShell attack (2012): Tens of thousands of student, faculty, and staff records were leaked as a result of a SQL injection campaign carried out by a mysterious organization known as GhostShell, which affected 53 colleges.
Turkish government (2013) — In a particularly daring SQL injection attack, debt records for utilities like gas, electricity, and water were deleted from a Turkish government web portal.
Flaticon (2020): To obtain the email addresses and passwords of 8.3 million Flaticon & Freepik users, a hacker collective conducted a SQL injection assault on the Flaticon website.
SQL Injection vulnerabilities
Tesla (214) — White hat penetration testers found that they could use SQL injection to obtain admin access to Tesla’s website and obtain private customer information.
Cisco (2018) — Potentially harmful access to shell systems was made possible by a hastily patched SQL injection vulnerability in Cisco’s software.
2019 saw the revelation of a Fortnite SQL injection vulnerability that could have compromised the accounts of over 350 million users, thereby upending the immensely popular online game.
MOVEit Transfer (2023) — MOVEit software developers discovered and fixed multiple SQL injection issues that might have allowed unauthorized database access.
The impact of SQL injection attacks
Attacks using SQL injection can result in a variety of outcomes. Both the targeted organization or company and individual victims may suffer greatly from a single SQLI assault.
SQLI effects for individuals
Although SQLI won’t specifically target you, using a website that has been attacked could have serious consequences. If you have an account on a targeted website and submit personal information, hackers can use that information for much more than just obtaining personal information.
SQL injection attacks can have serious repercussions for a person, including:
Money loss: A hacker may be able to take money out of your account by using SQLI on a bank or other monetary institution.
Identity theft: If a hacker gains admission to a database, they can steal its information and resell it on the dark web. This data can then be purchased by other fraudsters, who will use it to steal identities.
With Avast BreachGuard, you can protect yourself against identity theft attempts by having your data monitored on the dark web and receiving alerts if any websites you visit have been compromised by hacking or other security breaches.
SQLI effects for businesses
Businesses confront a far greater range of threats because they are the primary targets of SQLI attacks. A hacker with access to a database is capable of doing a plethora of tasks, and the business that is the object of this news will have no shortage of public relations damage control.
A few examples of how SQLI attacks can hurt companies are as follows:
- Sabotage: A hacker can quickly put a company into disarray by erasing its database or damaging its website.
- Theft of confidential information: A common goal of SQL Intrusion assaults is to get trade secrets, insider knowledge, protected intellectual property, and frequently, user or customer information.
- Security lapses: A hacker could be able to access other parts of an organization’s internal network by using the information in a database that has been compromised. The network as a whole might eventually be compromised.
- Reputational damage: It can be challenging for a company to win back the confidence of its clients and the general public following a SQLI assault.
Potential costs of SQLI attacks
The potential expenses can be high given the extent of what a hacker can accomplish using SQLI. According to a 2014 study, the financial consequences alone might make even modest SQL injection assaults cost up to $200,000 to fix.
The US Navy reportedly spent more than half a million dollars responding to a single SQL injection attack, according to an Ars Technica article that was published that same year. Additionally, for several months after the incident, more than seventy service members were unable to move forward with unfulfilled transfer requests. Also check Quizlet Alternatives
Apart from the monetary expenses incurred in handling an assault, a company’s reputation may suffer permanent long-term harm.
How can I prevent SQL injection attacks?
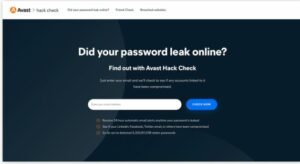
You cannot do it unless you are a web developer. You are not directly targeted by SQL injection, so there is no method for you to recognize, stop, or prevent an attack. Furthermore, you won’t become aware of a compromised website until after the consequences become apparent.
It is the responsibility of the people who maintain the websites you use to prevent SQL injection attacks. However, there are some things you can do to combat SQLI. Visit our free Avast Hack Check tool right now to see if any of your website’s login credentials have been compromised. If so, go to that website right now and change your password.
Use Avast Hack Check to determine whether any of your login credentials have been compromised. The Avast Hack Check tool allows you to determine whether any of your website login credentials have been compromised.
Since user data is frequently stolen by SQL injection attacks, one method to lower your risk is to employ Hack Check in case your data is ever compromised.
So, how can I avoid SQL injection?
Although it is impossible to stop SQL injection attacks from happening, you may lessen your vulnerability to them and lessen their repercussions if you are ever caught in one. Include the following safe internet browsing practices in your daily routine:
- Give no personal information to dubious websites. Rather, be sure that you only enter sensitive data on reputable websites with robust security safeguards. Although it’s a start, even this can’t ensure that you won’t be detected by SQL injection.
- Keep up with news about tech security. Businesses will notify the public if and when hacking attacks compromise their databases. Keep track of any updates about the websites you visit, and as soon as you see a report about SQLI, update your login information.
- Develop secure password usage practices. By creating different passwords for each account you have, you can lower your risk. To stay one step forward of the hackers, use strong password generating techniques.
- Make use of a password organizer. If you use a password manager, you can receive alerts when websites you visit are compromised. If that’s the case, switching between distinct, difficult-to-crack passwords will be a snap. Invest in a password manager that works across platforms so you can access your credentials from any device.
- Make use of antivirus software. A trustworthy antivirus program can defend your gadget from a variety of dangers, including nefarious websites.
Get comprehensive digital security with Avast One
You don’t have to take the lead in the ongoing fight against hackers, even though your browser won’t be able to tell whether you’ve visited a website hacked by SQL injection. It is necessary to summon the cavalry.
With Avast One, you can defend yourself against a variety of online threats by having many fronts of real-time cybersecurity. It will strengthen your network with a firewall and keep an eye out for malware traces in addition to keeping an eye out for vulnerabilities in your device, such as out-of-date software, dubious apps, phishing attempts, and so forth.