How To Spot Email Scams Complete Guide

How To Spot Email Scams will be discussed in this article. It would seem that scammy emails have vanished from the scene and that people are now digitally literate, able to distinguish between legitimate and fraudulent communications.
How To Spot Email Scams Complete Guide
In this article, you can know about How To Spot Email Scams here are the details below;
And while this may be partly true, frauds in general and email scams in particular have grown increasingly complex, making it more difficult to identify them:
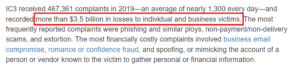
The figures above, which are based on FBI reports, represent the losses that individuals and companies endured in 2019. According to Avast Security Evangelist Luis Corrons, “It was a year of phony news and scams, tricking users while taking benefit of the pandemic,” as far as we know, this number climbed significantly in 2020.
Generally speaking, emails intended to harm a person or a business are considered email scams. Their goal can be to defraud the receivers of substantial sums of money or get vital information, such as passwords and bank emails. Naturally, a con artist would also wish to target other types of information, such as social security numbers, email lists, and even private data like phone numbers and home addresses.
Scammers typically utilize tactics to incite fear or present an irresistible offer to their victims, such as an opportunity to invest or an exceptional bargain on pricey goods.
How to recognize emails that aren’t a scam
For most users, it might be difficult to identify emails that are not part of a sophisticated scam. In particular, certain actions that one would assume con artists wouldn’t commit are more likely the result of conjecture than fact.
The email address, language, and grammar utilized, however, are not up for debate. More particular still:
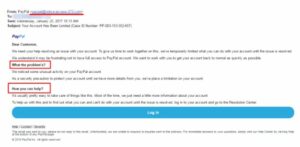
It is unlikely that this email is still valid because it is not a valid email address. In this instance, it would be wise to ascertain the kind of behavior that might have resulted in the sending of this email.
Scammers rarely, if ever, have the long term in mind; instead, they are usually in it for the fast money. which implies that they don’t typically use components like customization.
Subtlety is another tool that con artists will not employ. Conversely, they will employ terms such as “URGENT,” “EXCLUSIVE,” and so forth.
Of fact, a lot of email marketing initiatives commonly include a time limit. In actuality, the majority of email marketing solutions come with features like countdown timers that can add some flavor to your email campaigns.

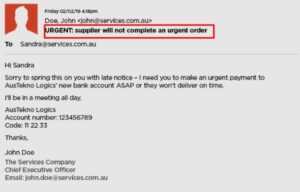
Words like “Your account is at risk” or “Urgent action required” will not go over well with your recipients. This seems like classic con language, especially if it’s very impersonal and general.
Unlike scammers, marketers employ strategies that reduce, if not completely eliminate, suspicion and let consumers know that they are interacting with a legitimate company. Examples of these strategies are trigger emails and truthful, individualized content that prioritizes the needs of the user.
The different types of emails scams
Let’s discuss the components of scammy behavior before delving into the many kinds of email scams and how to identify and safeguard your account.
Con artists will:
- attempt to deceive recipients into providing vital information and passwords by pretending that a dire (and extremely serious) emergency is approaching.
- Use terrible grammar
- Claim to be associated with a well-known company or a trustworthy contact’s partner; claim to require more elaborate and sophisticated procedures than a well-known brand would (such as faxing scanned papers or phoning a certain phone number); but let’s be a little more detailed.
What is phishing in emails?
Email phishing is the most prevalent type of digital scam.
Phishing emails aim to trick recipients into falling for a fraud by requesting sensitive information such as passwords to secure websites or bank account information.
Because phishing is based on human behavior, it is incredibly effective. The con artist employs strategies to trick others into thinking that there is an urgent issue that calls for them to take immediate action.
Users are compelled to give up sensitive data or make online payments because they feel like they are in immediate danger.
What is spam?
Although spam emails aren’t always harmful, they could be. They are typically neither segmented or personalized and are meant for a wide number of recipients, primarily for commercial purposes.
The fact that the brand or individual contacting the receiver hasn’t naturally developed an email list is the reason they might be hazardous. Conversely, your information, along with the email list’s entire content, may have been mined or sold for a high price.
What are email scam?
As previously indicated, the goal of email scams is to deceive users into divulging information that could endanger them in a variety of ways.
Email scams may be extremely detrimental to a person’s wellbeing, ranging from causing psychological and physical injury to identity theft or making false accusations at unlawful behavior.
What is spoofing?
Spoofing scams can produce an email address that is nearly exact replicas of a well-known brand that people are likely to connect with, including with email content that features the business’s logos and colors. At first sight, these addresses—such as “@venrno.com” in place of Venmo and so forth—might appear to be authentic.
These emails typically include a link that, if clicked, could cause the recipient to download malware or reveal personal information and forfeit a sizable portion of their assets.
What is malware?
Software known as malware is created with the intention of accessing a computer and obtaining information, such as passwords. Scammers can watch, change, and eventually steal critical data thanks to this access.
Typically, a questionable sender address results in people receiving emails containing dubious links or attachments. Requests are made in this email for users to download the branch or click the link as part of a routine that might resolve a potentially “threatening” issue.
How to ensure you’re protected every step of the way
The best defense against scam email campaigns is for people to become well-informed and understand the true nature of scams.
Here are the steps to take in the interim.
Use backups and two-factor authentication
In addition to protecting user data, two-factor authentication and backups can also inform consumers of what to expect. Information can be kept safe with backup software, so even in the event that the computer sustains significant damage, the user won’t find themselves without any data on their computer.
However, when there is questionable log-in behavior or a password change, the user will receive a notification from two-factor authentication. Two-factor authentication makes sure that the activity is motivated by a user action by requesting verification and authentication from the user.
Keep your OS and antivirus updated
The operating system (OS) on a computer must constantly be current. An outdated operating system version’s security measures may be superseded by certain scam techniques. This is especially true in light of the fact that an operating system (OS) can be often attacked, primarily via phishing emails and outdated internet browser versions.
An updated version of the antivirus program does the same thing. Computers can be shielded against malware updates by using antivirus software.
How to spot an email scam
As previously stated, the first and most crucial line of defense is being aware of the characteristics of an email scam and how to spot them.
Users should be aware that spam emails typically contain little errors in addition to double-checking the sender’s email address and pointing out discrepancies between addresses and domain names.
The main focus of these errors is on grammar, syntax, and spelling. The intricacy of the fraud influences how subtle it is.
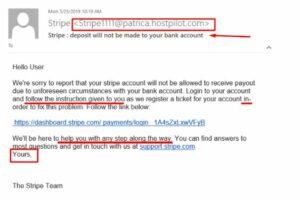
This fraudulent email is sufficiently nuanced for a user to be duped by a cursory glance. Still, one of the telltale signs is the sender’s address.
The salutation is the same. The greeting “Hello user” is highly unusual in the age of smart lead nurturing and personalization. Furthermore, the user is asked to click on a dubious link in this email even though they are not asked to divulge a crucial password.
When an unsolicited email arrives with odd-looking links and attachments, it should always be regarded as suspect, even if the recipient doesn’t know the sender’s address.
Other types of attacks to keep an eye for
Email scams can occasionally be the icing on a carefully planned, comprehensive scheme. Users must thus stay informed about the latest online threats.
HTTPS phishing attacks
Users often believe that connections and websites that employ HTTPS are trustworthy and safe. This is no longer the case, though, as con artists employ this protocol to make phishing emails appear authentic and reliable in their connections. Also check how to block spam emails
Make sure the link you are going to click is the actual website link that you are being asked to visit, not one that has been shortened. Additionally, keep an eye out for hypertext; the email’s “safe” URL can actually be plain text that points to a fraudulent website.
SMS phishing, also known as smishing, is an attempt to trick someone into sending sensitive information, such as credit card numbers, by infecting their device with malware via text message. The texts typically have a link that takes the recipient to a page where they are asked for personal information, and they seem to be sent from a reputable company or individual.
Phishing on social media is another way con artists can get private information that they might use to target individuals with other frauds. Scammers may employ social engineering strategies to build social proof and gain consumers’ trust, such as making exaggerated claims during partnerships with Instagram influencers.
Vishing (voice phishing)
Vishing is a phone-based method of obtaining data. Scammers typically want the victim’s credit card information, but occasionally they may also want to steal identity.
Scammers will typically use a dialer to generate a random number and “bait” the caller by saying there’s a problem with the victim’s credit card or possibly with another family member. In this manner, the victim feels compelled to act right away.
The takeaway
Users frequently find themselves in a tricky situation when they are unsure of whether to trust an email address that is requesting that they take immediate action.
In the era of sophisticated digital marketing, it’s critical to keep in mind that not everything is as it seems. Emails requesting specific actions that require data, rather than being the result of a specific user activity, may be scams.
This poses a risk to the health of your computer and its operating system—Windows or macOS, for example—because both systems are susceptible to malware infections.
The aforementioned data highlights how important it is to use marketing automation, email marketing, and up-to-date antivirus software.