Essential Guide To Phishing In 2024

Best Essential Guide To Phishing will be discussed in this brief article. Phishing is a cybercrime tactic that trick victims into clicking on dangerous links or divulging private information by using fraud and deceit. Understand how it operates to protect your data and identify and stop phishing frauds. Then, use industry-leading internet security, such as Avast One, to be safe from phishing scams and other online dangers.
Essential Guide To Phishing In 2024
In this article, you can know about Guide To Phishing here are the details below;
What exactly is phishing?
Phishing is the practice of an attacker tricking a victim into divulging personal information or clicking on a harmful link by means of social engineering techniques.
This Article Contains:
- What is phishing, exactly?
- How is phishing carried out?
- Phishing emails: the basics
- What kinds of phishing scams are there?
- Defend yourself from phishing with Avast
- What kinds of phishing assaults are there?
- In what way do you respond to phishing emails?
- The best ways to avoid phishing
- Obtain protection that leads the market to help prevent phishing assaults.
A phishing assault has three parts:
- Emails and phone calls are examples of electronic communications that are used in the attack.
- The attacker assumes the identity of a person or group that you may trust.
- The objective is to get sensitive personal data, such as credit card digits or login credentials.
One of the oldest & most well-known frauds on the internet is phishing. The term “phishing” originates from the practice of hackers using an alluring lure to lure victims out of the wide pool of internet users. The origin of the word “phishing” (pronounced “ph”) is the mid-1900s pastime of “phone phreaking,” in which amateur “phreaks” would play around with telecom networks to see how they operated. Fishing plus pheaking equals phishing.
Spam vs. Phishing
The main distinction between phishing and spam is that the former doesn’t always aim to harm you. Junk mail, or unsolicited advertisements, is what spam is most commonly. In contrast, phishing is evil since its perpetrators aim to steal your personal information and utilize it against you. Of course, spam communications can also be used in phishing assaults, so you should still stay away from them.
There are other threats that can steal data than phishing. You also need to be on the lookout for spyware. Find out how to get rid of spyware from PCs, iPhones, and Android devices.
Latest cybersecurity news – November 2024
- Current phishing trends: CAPTCHAs, steganography, and QR codes | Hacker News
- Targets of a large phishing campaign are OpenSea NFT users – CoinTelegraph
- Large-scale phishing supplier shut down by police | Bleeping Computer
- Traditional multi-factor authentication is insufficient to thwart phishing assaults | TechTarget
- Hackers take over Bloomberg’s Twitter account to direct users to phishing malware | TechRadar
How does phishing work?
Phishing operates by sending a targeted advertisement to victims with the intention of convincing them to click on a link, download an attachment, provide the needed information, or even finish a payment. All phishing assaults adhere to the same fundamental guidelines, regardless of the channel they use—email, social media, SMS, or another.
Phishing attacks can occur via phone calls, social media, email, or SMS. They can also occur on any computer device.
What phishing is capable of is determined on the creativity and expertise of the phisher. Because social media is so widely used, phishers now have more personal information about their targets than ever before. Equipped with this wealth of information, phishers may customise their attacks to the unique requirements, preferences, and situations of their victims, making their offer even more alluring. In these situations, social media encourages the use of social engineering to carry out phishing episodes more successfully.
After elucidating the operation of phishing schemes, let us examine their consequences concerning you and your information.
What are the effects of phishing?
In addition to being a useful tactic for corporate espionage and data theft, the majority of phishing assaults can result in identity or financial fraud. Some cybercriminals would even go so far as to make fictitious social media accounts and spend time getting to know potential victims before setting them up for success.
How much does phishing cost? Not only monetary losses, but a loss of trust in these situations as well. Being conned by someone you trusted is painful, and getting well again might take a while.
Email phishing 101
Via email, phishing attempts are frequently carried out. You have most likely encountered phishing emails in your mailbox, as they are among the most common forms of email fraud. Let’s explore some of the most prevalent frauds and learn what email phishing is.
What is a phishing email?
A phishing email is one that attempts to trick you into divulging personal information or infect you with malware through attachments or links to nefarious websites. Phishing emails frequently imitate the precise wording, logos, images, and formatting of reliable email sources in order to appear authentic.
What does a phishing email aim to accomplish? Phishing emails, like other forms of phishing, use cunning social engineering techniques to deceive you into disclosing personal information.
What are the most common phishing emails?
The majority of phishing emails fall into one of many groups. Here are a few of the ones that you probably will see:
- Problem with billing or invoice: You will be notified that there is a billing issue preventing the shipment of an online purchase you made lately. Clicking through will send you to a fake landing page where you’ll be asked to provide your bank information, at which time the phishers will obtain it.
- These emails play on your tendency to believe demands from people in positions of authority and comply with them, which is how the government is trying to reach you. This type of phishing email is usually intimidating, promising a terrifying penalty if you don’t provide them the needed personal information.
- Think of this as the opposite of the last example: the government wants to give you money. These emails, which appear around tax season, promise you a tax refund if you can verify your financial information right away.
- A cry for aid: Cybercriminals will assume the identity of a friend or family member, claiming to be in a terrible situation and pleading with you for money. Through phishing phone calls, these schemes are frequently carried out against the elderly.
- The bank alert: If they see any questionable behavior or if a customer’s account is likely to become overdrawn, many banks will notify the customer. Phishers attempt to get victims to “confirm” their bank account details by using these useful services.
- You’re the big winner: Phishing emails frequently make the claim that you are the fortunate recipient of a fantastic gift. Entering your information is all that’s required to collect your prize.
- Urgent business: Phishers like taking advantage of your haste to make poor selections. Their goal is to intimidate you into providing your personal information as soon as possible, whether that is through a temporary offer that seems too good to be true or a threat to delete your account if you don’t act.
- An example of a phishing email that seems like it comes from Amazon is this fraud.
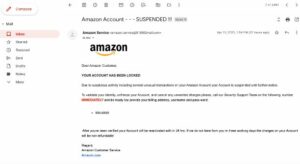
What does a phishing email look like?
Even though they can take many different forms, you can understand how to spot phishing emails. As your first line of defense against phishing, keep an eye out for the following warning signs:
- The email isn’t meant for you: Phishing attacks can take many different forms, one of which is the common “deceptive phishing” technique. As a result, the email will not be addressed to you personally and will instead begin with a generic greeting like “Dear Customer” or possibly even your email username. Reputable businesses will use your name in official correspondence.
- An offer you can’t turn down: If a deal or offer appears too good to be true, it most likely is. Refrain from falling for these con artists’ enticing proposals. Don’t fall for anything they’re promising.
- Need for immediate action: As previously noted, phishers place a strong emphasis on urgency. Most importantly, resist the urge to become alarmed and resist giving in to FOMO or believing threats. No respectable organization, be it corporate, governmental, or otherwise, will give you a split second to take action before shutting the door.
- Link-shortening services may conceal harmful links, so be cautious when clicking on them. Generally speaking, mouse over all links before clicking. When checking emails while on the go, take extra caution when clicking links because the majority of mobile interfaces lack this feature.
- In their phishing emails, hackers will entice you to click on links that are spoofs of authentic websites with very identical URLs. Keep an eye out for intentional misspellings that include letters and characters that appear similar, or typosquatting, which is when hackers trick you by using a slightly erroneous version of the official URL. Before clicking, carefully read the links!
- Poorly written: You won’t receive an email from your bank that is full of typos and grammatical errors. However, a phisher may and frequently will. These kind of careless mistakes are fatal giveaways of a phishing email.
- Attachments: In general, if they come from a trustworthy source and are expected, there is nothing wrong with attachments. Away from this setting, avoid unidentified attachments. Malware can even be concealed by scammers in rich-content files like PDFs.
- We need your personal information because phishers are chasing it. You’re probably being phished if you’ve received an email requesting you to validate your login information, account details, or other personal data.
- You don’t utilize this business or service: Phishers typically send out their phishing emails to as many people as they can because they don’t have access to the user databases of the organizations they spoof. If you are a devoted supporter of Content Streaming Services B and C and you have gotten an email from Content Streaming Service A, it is probably phishing.
- An attempt to persuade recipients that their Google account has been compromised using phishing emails
- I really received the email mentioned above in my personal inbox. I imagine that if I had fallen for this scam and answered the email, I would have been prompted to enter the login information for my Google account.
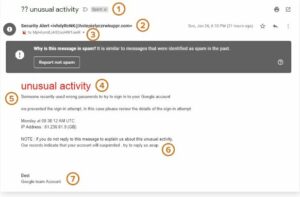
Observe how many of the cautionary signals covered above are present in it:
- informal subject line written in
- emailed from a dubious address
- The recipient isn’t the real email address you use.
- Not addressed to the recipient in the email
- The email content contains grammatical and other language mistakes.
- Requested is immediate action.
- Without the standard signature text that one would anticipate from a professional email
What the experts say
“Anyone who receives these emails is advised to delete them. Do not click on any links or attachments in messages if you are unsure if they are real or not. Instead, visit the company’s website and use the contact details provided there to get in direct contact with them, as that is where the message appears to have originated.
Panel Novak, Junior Threat Operations Analyst
Threat Avast Labs
What are the different types of phishing scams?
Let’s investigate a little more to learn the specifics of phishing. What might be the source of a phishing assault and how might it appear? It’s time to find out some answers.
Phishing vectors: more than email
Any communication channel can be used to phish you, therefore websites, text messages, phone calls, and emails are all real and active phishing vectors.
- Email phishing: The most popular technique, email phishing sends the phishing bait via email. These emails frequently include attachments with malware or links that point to nefarious websites.
- Phishing websites, commonly referred to as faked sites, are phony replicas of well-known and reliable websites. These fake websites are created by hackers in an attempt to trick you into giving them your login data so they may access your entire accounts. Another typical source of online phishing is pop-ups.
- Vishing is the aural equivalent of internet phishing, sometimes known as “voice phishing.” Over the phone, the attacker will make an effort to persuade the targeted parties to divulge personal information that might be used to steal identity. A lot of robocalls are efforts at vishing. In addition to vishing, find out how to halt phone spoofing.
- Phishing using SMS is known as smishing. You’ll get a text message requesting that you open an app or click on a link. But if you do, you’ll fall victim to a scam where malware is downloaded onto your phone, taking control of your personal data and sending it to the attacker.
- Phishing on social media: Some attackers have the ability to infiltrate social media accounts and coerce users into forwarding harmful links to their friends, followers, or other social groups. As part of a romantic scam, other attackers fabricate profiles and use these personas to conduct phishing attacks.
- Find out how to remove a virus from your PC, Mac, and iPhone if you find yourself with malware on your device.
SMS, sometimes referred to as “smishing scams,” is one of the phishing vectors.
Common phishing strategies
The main phishing routes mentioned above allow hackers to launch a variety of assaults. Some typical phishing techniques to get your information or take control of your devices are as follows:
- Phishing that is meant to deceive you is known as deceptive phishing, but there are a number of ways to do this off. Although the term “deceptive phishing” may appear overused, it relates specifically to the practice of hackers impersonating trustworthy organizations or people in an attempt to win your trust.
- Spear phishing: When an attacker tailors their attack to target a particular person, it is known as spear phishing. This is in contrast to large-scale phishing efforts, which resemble industrial fishing boats scouring the ocean with enormous nets. Since hackers can readily obtain all of your employment information in one location, professional social networks like LinkedIn have made spear phishing a common tactic used in corporate cybercrime.
- Whaling: Whaling is a type of phishing assault that goes after important people. Whaling assault risk extends to C-suite executives as well.
- CEO fraud: Phishers will pose as the CEO or another senior leader of a company in order to obtain payment or insider information from staff members. Following whaling assaults, CEO fraud operations are common, particularly if the attacker has already stolen the CEO’s login credentials.
- Phishing and farming are examples of phishing attacks. Phishing attacks use technological tactics to trick you instead of using bait. One pharming tactic is DNS cache poisoning, which can automatically reroute you from a trustworthy website to one that has been spoof-hosted by an attacker. It will be too late for you to detect the fraud if you’re not paying attention.
- Popular cloud services like Dropbox and Google Docs are prime candidates for phishing. Once you submit your credentials, attackers will create fake versions of the login panels, collect all of your files and data, and take advantage of you.
- Phishing clone: Attackers can take a valid email and clone it, sending the exact same email to all of the prior recipients with one important difference: the links are now dangerous.
- Link manipulation: When a link is sent by a phisher, it looks like it leads to one URL, but it actually goes somewhere else. Typical ploys include purposeful misspellings (for example, “only” instead of “onIy,” where the latter has a capital I) or using the name of a reliable website as the link’s display text. Another name for them is homograph assaults.
- Cross-site scripting: Skilled hackers can take advantage of flaws in a website’s scripts to take control of the site and use it for their own purposes. Because the URL and security certifications on the website seem to be authentic, it is difficult to identify cross-site scripting.
Hackers frequently impersonate representatives of well-known websites and services to trick their victims. These phishing scam types consist of:
- Scams involving phishing on Instagram
- Phishing Scams on Amazon
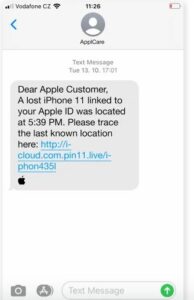
- Phishing Scams Using Apple ID
- Scams involving PayPal’s Phishing
Protect against phishing with Avast
Beyond just shielding you from malware and viruses, Avast One offers much more. Phishers love to utilize dangerous links and infected attachments against their targets, and our intelligent threat detection can identify these and alert you to their presence. Phishers cannot steal your data if they are unable to trick you, and we are committed to making sure that doesn’t happen.
What are some examples of phishing attacks?
There have been several noteworthy instances of phishing attacks during the 1990s. The following are a few old and current instances of phishing attacks:
AOL (the first notable attack)
In 1994, America Online (AOL) subscribers were the first victims of a phishing attempt that was documented. Through the use of a hacking toolset known as AOHell, scammers were able to pose as AOL staff and send consumers direct messages. Users were asked to confirm their accounts by providing their passwords or other credentials in these communications.
Facebook and Google invoice scam (one of the most costly)
A Lithuanian guy by the name of Evaldas Rimasauskas was able to defraud Facebook and Google out of over $120 million between 2013 and 2015. He did this by using a phishing scam that used counterfeit email accounts belonging to Quanta, a Taiwan-based company that does business with both corporations.
The IT companies would get well constructed phishing emails from Rimasauskas and his associates, containing fictitious contracts and invoices that would bill them for millions of dollars.
Twitter VIP breach (one of the most high-profile)
The victims of the 2020 Twitter (now called X) hack were well-known, which made the incident noteworthy. Social engineering was employed by hackers to obtain credentials from specific employees. Afterwards, a number of well-known Twitter accounts, including those of Elon Musk, Joe Biden, and Barack Obama, were taken over by the hackers.
Activision data breach (a recent example)
Activision, a publisher of video games, revealed in early 2023 that a smishing attack on one of its employees in late 2022 had resulted in a data leak. Employee information, such as emails, phone numbers, and work locations, was compromised by attackers. Although Activision asserts that they swiftly stopped the hack, the information obtained might still be applied to social engineering schemes in the future.
How do you deal with phishing emails?
It’s easy: just report and remove! There should be a feature in your preferred email service that lets you report phishing scams to them directly.
Next, forward the emails to [email protected] for the Anti-Phishing Working Group and [email protected] for the Federal Trade Commission. Visit the FTC’s complaint website to report your encounter with phishing as well.
Finally, get in touch with the firm that is being impersonated to assist spread the word that a phisher is trying to defraud people by exploiting their brand.
Identity theft is a possibility when phishing attacks use stolen data. In order to lessen any damages and prevent identity theft in the future, if you have already been a victim, understand how to report identity theft.
It is recommended that you report and delete any phishing emails that you come across.
Top tips to prevent phishing
Anti-phishing software and thorough internet security training provide an effective two-pronged organizational defense against phishing. Employers ought to spend money training staff members to recognize phishing scams. With the use of powerful software countermeasures, security professionals can reinforce these recommendations and stop phishing frauds.
Here are some personal defense mechanisms against phishing scams:
- Become knowledgeable: Fortunately, you’ve already done this step by reading this article. Continue to keep up with the most recent frauds and schemes to stay one step ahead of phishers. Bring attention to your coworkers, family, and associates as well.
- Be skeptical: When dealing with any questionable email, err on the side of caution. Examine the phishing warning signals listed previously in this post before opening any attachments or clicking any links. Please report and delete the email in question if any of these apply.
- Verify before you take action: Reputable businesses will never call or email you to obtain personal information. In the event that this occurs, verify anything stated in an email or phone conversation with the business by calling them directly, using the number listed on their official website. Avoid directly responding to shady communications. Always use the formal channels of service provided by the company to start a new conversation.
- Check websites: Unless you are certain that a website is secure, don’t enter any personal information that you wouldn’t want a hacker to obtain. Your data may be stolen by data brokers and online tracking. Use the greatest encryption software to help protect your online data because nearly three-quarters of phishing attacks utilize a URL that starts with HTTPS.
- Regularly change your passwords to prevent phishers from using them for malicious purposes. Use a password manager to develop secure passwords & store them safely, and change your passwords on a regular basis.
- Employ two-factor authentication (2FA): By demanding a second form of verification in order to access your account, 2FA increases account security.
- Examine your financial statements closely and check your accounts to ensure you don’t overlook any fraudulent charges. Although credit cards and banks are typically rather good at spotting fraud, you should still keep a careful eye on your accounts and records.
- Employ an ad blocker: This advice may also read, “Don’t click pop-ups,” but the majority of pop-ups will be blocked before you see them if you use one of the finest ad blocks. If you encounter a pop-up window, avoid clicking anywhere within it, even if it has a large “close” button. Pop-up windows are typical phishing targets. Utilize the small X in the corner at all times.
- Use this handy tip to identify phishing email schemes: read emails in plain text. If you convert an email to plain text instead of HTML mode, you will be able to identify hidden picture URLs.
- Use security software: To automatically identify phishing attacks and stop you from falling for them, the ideal internet security software will include a reliable antivirus program and a secure web browser. It is insufficient to merely use Windows Defender. The greatest privacy and security iPhone applications can help you stay safe because even iPhones are vulnerable.
- Put an end to spam: Although unsolicited texts and emails are primarily just bothersome junk mail, con artists may use them to distribute phishing emails. Find out how to modify your privacy settings to prevent unsolicited emails and texts.
- Be careful what you share online. Keep your disclosures to a minimum and delete any personal information that might be used by hackers.
Get industry-leading protection to help avoid phishing attacks
If you delegate most of the job to a trustworthy anti-phishing solution, you’ll have a lot less work to complete. Before they can reach you, Avast One identifies and prevents phishing attempts. Furthermore, it updates immediately whenever a new attack is detected, giving you real-time protection against the constantly changing danger landscape of the internet.