Best Ultimate Guide To Identity Theft In 2024

Best Ultimate Guide To Identity Theft will be discussed in this article. A major criminal that impacts millions of individuals annually and frequently more than once is identity theft. Our comprehensive tutorial will explain identity theft, tell you how to prevent it, and demonstrate how you can prevent data theft right now with a powerful privacy and security solution like Avast One.
Best Ultimate Guide To Identity Theft In 2024
In this article, you can know about Identity Theft here are the details below;
What is identity theft?
Identity theft is a criminal offense whereby an individual obtains your personal data, typically with the aim of committing financial fraud. Identity theft encompasses a wide range of fraudulent activities involving personal information, from money theft to the use of a victim’s information for credit applications or medical treatment.
This Article Contains:
- Identity theft: What is it?
- Identity theft types
- Identity theft: Is it illegal?
- The process by which identity theft occurs
- To what extent is identity theft prevalent?
- How can I tell if person has stolen my individuality?
- What to do in the event that identity theft occurs to you
- How to guard against theft of identity
- Use Avast to keep a close eye on your personal information.
Hacking into someone’s social network account is a relatively easy identity theft, but it can also involve more intricate actions like filing tax forms under someone else’s name. Identity theft is more common than ever since so many people freely share personal information online.
Identity fraud frequently results from identity theft, where the criminal assumes the victim’s identity or takes action on their behalf. Numerous victims of fraud and identity theft struggle for years to piece together the crimes, with no assurance that their losses will be completely recouped.
Types of Identity theft
Depending on the type of personal data obtained and how the thief utilizes it, identity theft can encompass a wide spectrum of criminal activities. Complete names, social security numbers (or other government-issued IDs), and financial information are typically taken in data breaches. Regarding the definition of identity theft, the majority of these crimes can be classified into one of three main categories.
Financial identity theft
The most prevalent and simple kind of identity theft is financial identity theft, which occurs when someone uses a victim’s information to obtain money falsely. Being a direct loss to the victim makes it one of the most harmful forms of identity theft.
These are just a few instances of how financial identity theft can occur. A financial identity thief may: Depending on the data they take and its intended use,
- Proceed to another bank account to make a transfer of funds.
- Engage in a “account takeover” by adding their name to your bank account.
- Get your tax return by filing false tax documents.
- Acquire credit or loans in your name.
- Use your recognition card or other payment details to make purchases.
Criminal identity theft
While all identity theft is illegal, criminal identity theft describes circumstances in which someone assumes your identity in order to evade prosecution. This typically occurs when someone provides the police with incorrect information after being taken into custody.
Criminal identity thieves may possess a phony ID or official government documents that they got fraudulently using the information of their victims. It might be challenging to prove your innocence to the authorities and clear your name if someone is committing crimes in your name, particularly if they are unable to identify the true offender.
Since many victims of illegal identity theft first learn about it by accident—for example, during a background check by an employer—the ramifications might last for years.
Medical identity theft
The act of someone receiving medical treatment under your name is known as medical identity theft. Medical identity theft is particularly dangerous in nations like the US that have for-profit healthcare systems because the incentives to commit medical identity theft are great and healthcare costs can rise rapidly. However, medical identity theft is also utilized in other nations to give thieves access to pharmaceuticals or medical care that they may not require.
The victim may then be refused treatment when they seek medical attention on their own because the thief has already received it. The medical history of the thief may also be included to the victims’ own medical file.
Child identity theft
The most pernicious kind of identity theft is probably child identity theft, which happens when someone takes a child’s identity and exploits it for any of the purposes listed above and more. They might apply for credit, purchase real estate, or obtain official government documents using a child’s social security number or other kind of identification.
Children’s identities are important to anyone seeking for a clean source of credit because they usually have no debt or credit. Unfortunately, because so many people have access to the children’s information, there are a lot of examples of child identity theft that occur within foster care systems.
Is identity theft a crime?
Of course! Similar to other forms of theft, identity theft is a prohibited and unlawful conduct. Identity theft is also a form of cybercrime because it frequently occurs online, which means that identity thieves are now cybercriminals.
Identity thieves are interested in your personal information because they can use it to open new accounts, purchase products or services, apply for credit and loans, obtain legal documents in your name, avoid prosecution, and commit a host of other crimes.
How identity theft happens
Identity thieves may complete their work much more easily thanks to the internet. We enthusiastically share details about ourselves online all the time, whether it be on social media or an e-commerce site. Our birthdays, careers, hometowns, relationships, and more are all out there in the public domain, ready to be exploited.
Data breaches
Hackers take private information from a company’s servers or databases, resulting in data breaches, also known as data leaks. Hackers have the option to sell user or customer data, which may include social security numbers, other ID numbers, passwords, addresses, passport numbers, credit card information, and more, to identity thieves if they are able to breach the company’s security and gain access to it. Companies that gather and sell personal data, known as data brokers, are frequently the targets of data breaches.
You may check if any of your passwords have been compromised by using the free program Avast Hack Check. Give it a go!
You may check if your personal information has been compromised for free with Avast Hack Check.
Smaller data breaches occur on a daily basis, but larger ones—like the 2017 Equifax breach, which exposed the personal information of over 150 million people—occasionally make headlines. The information that our identity thieves can obtain is typically uploaded and sold on the dark web by hackers who have taken advantage of a data breach.
The dark web
Following a data theft, the perpetrators must monetize the stolen information, which is where the dark web enters the picture. The dark web is a portion of the internet that can only be accessed with technical software, such the Tor Browser, and is not accessible through regular Google searches. Additionally, because search engines do not index the dark web, you must be aware of your destination.
However, if you’re knowledgeable, as many identity thieves are, you may purchase reams of stolen data. This is where Avast BreachGuard comes into play; we continuously search the dark web for any indications of your data, and if we do, we promptly notify you. In this manner, you can take preventative measures to safeguard yourself before identity thieves can purchase your data and utilize it against you.
Social media
How many websites need you to create security questions that you can respond to in the event that you lose your password? Many of these responses align readily with our social media content, which is convenient for hackers. Which primary school attended by you? This is a simple answer if a potential identity thief is aware of your childhood home; if they can correctly answer your questions, they can easily access your account.
Examine your Facebook, Instagram, and other social media accounts’ privacy settings, and think about making them more private.
Phishing and pharming attacks
Phishing and pharming scams are some techniques identity thieves may employ to trick you into disclosing private information. Phishing assaults entail enticing a target with communications from a spoof social network account or with bait, such as a cunning email that seems to be from a reliable source. You run the danger of giving the attacker the information they need to steal your identity if you respond.
Phishing and pharming are similar, although phishing is much more widespread. Pharming assaults, as opposed to phishing bait, subtly steer users to phony websites that are made to appear like trustworthy, authentic websites. You run the danger of providing the attacker with your personal information if you try to log in or do other tasks when you get there.
Always follow sensible email and internet safety procedures since social engineering and deception are the foundations of both phishing and pharming assaults.
Malware
A common weapon used by identity and data thieves, among other cybercriminals, is malware, or malicious software. Spyware, for example, is a particularly good sort of malware for the task since it can surreptitiously record your internet activity and gather data. Spyware allows hackers to covertly gather all of your private information without even letting you know that they have compromised your phone or computer.
You are protected by Avast One’s round-the-clock malware detection, blocking, and eradication. You’ll be protected from future attacks and any malware that may have previously been on your machine will be instantly eradicated. Additionally, the integrated Web Shield and Email Shield will identify and stop any dangerous attachments or links used by phishing emails in an attempt to trick you.
Additionally, Avast One comes with a plethora of privacy measures to guarantee the protection of your personal information.
Email hacking
Once an identity thief has your email password, they can go through your correspondence to gather a variety of personal data. To get even more information on you and your contacts, they can even send emails to other individuals pretending to be you.
Passwords acquired by identity thieves are typically purchased on the dark web by other crooks. Then, assuming the role of email hackers, they can access your account by using phishing, malware, and even a variety of password breaking tools.
Use a strong, one-of-a-kind password that combines letters, numbers, and symbols to secure your email account (or create a random password), and change it often to keep hackers guessing. When using a computer that you don’t own, always log out after checking your email. Additionally, keep track of all your passwords by using a reliable password manager.
Wi-Fi hacking
We frequently discuss the need to exercise caution when using unprotected public WiFi, and the reason for this is that anyone can park their computer on a public Wi-Fi network and eavesdrop on others with minimal hacking experience and access to the necessary equipment. Public Wi-Fi is like an unlimited banquet to a data thief, and they are back for their fifth helping.
Hackers can quickly access your home Wi-Fi router if it isn’t securely locked with a strong password. If a hacker gains access of your router, they could potentially install malware such as sniffers that gather data or reroute your traffic to websites that promote false information.
Employing a VPN, which encrypts all of your internet traffic—even on dubious networks—you can safeguard yourself when using unprotected Wi-Fi. When utilizing public Wi-Fi, you have to make sure you’re using a trustworthy VPN, such as Avast SecureLine VPN.
Unsecured browsing
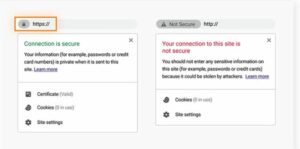
If you have the strongest password in the world secured against hackers, your network may still be leaking data due to your browser. Therefore, always check for a small padlock icon in the speech bar of your browser before entering personal information into any website. The padlock indicates that HTTPS encryption is in place on the website you are visiting, safeguarding your information both during transmission and reception.
Check for HTTPS encryption to determine if a website is secure. The website on the left is secure and has HTTPS encryption, whereas the website on the right does not.
If your website doesn’t use HTTPS, you run the risk of having someone snoop on your traffic. This applies to your internet service provider (ISP), your government, and the Wi-Fi hackers mentioned above.
Additionally, HTTPS indicates that you are (probably) linked to a trustworthy website. Instead, a lot of pharming websites will employ standard HTTP. Check for HTTPS the next time you enter into your online banking account; if you don’t see it, there’s a serious reason to be concerned.
When you connect to websites, our free Avast Secure Browser requires HTTPS encryption. Your traffic will be protected from prying eyes even if it is directed to an insecure website. Avast Secure Browser has a plethora of integrated security-enhancing features, one of which is this automatic HTTPS encryption.
How common is identity theft?
Identity theft regrettably occurs far too frequently. In the US, 444,602 identity theft reports were introduced to the Federal Trade Commission (FTC) in 2018 alone. Since 2008, the number of yearly reports of identity theft has increased by 41%. Credit card fraud, or the act of an identity thief opening a new credit card in someone else’s name, accounted for more than 35% of the reports that were received.
Meanwhile, 21% of victims in the US experience numerous identity theft incidents annually, according to the Center for Victim Research. Due to the fact that many victims are successfully targeted more than time, the true number of victims in the US is closer to 7 to 10% of the population.
How do I know if I’m at risk?
Identity theft affects everyone, but some people are more vulnerable than others. Identity thieves target those who are less inclined or unable to keep a close eye on their bank accounts. They’ll also search for users who have poor internet security practices, such as those who reuse their passwords across several accounts.
The following categories of people may be more vulnerable to identity theft.
- Young persons beginning their journey toward financial independence, such as college students and recent graduates, might lack the experience necessary to recognize frauds and phishing attempts. Additionally, they frequently overshare on social media, which can reveal important information.
- Children: Since identity thieves are drawn to victims with spotless credit records, kids make perfect targets. It’s possible that kids are less adept at spotting online dangers.
- Seniors: Identity theft and other frauds commonly target the elderly population. They are vulnerable to being taken advantage of by their caregivers, just like kids are.
- Wealthy individuals and company owners: A large haul is always appealing to thieves. Because they may be able to make a bigger profit and because they may have access to sensitive company information, identity thieves tend to target those with advanced degrees, better incomes, and more net worth.
- Deployed service members: Those who are unable to monitor their money on a regular basis, such as active military members, are more vulnerable to identity theft since they could not become aware of questionable activities until it is too late. Even family members and friends who know that deployed service men won’t be returning home for some time target them.
- People who are incarcerated: Similar to active military personnel, those who are incarcerated may find it difficult to do routine credit and financial checks. They may also be more susceptible to identity theft by friends and relatives.
- The deceased: An enterprising identity thief is not deterred by the mere threat of death. “Ghosting” is the practice of taking on the identity of a deceased person. If no one is looking, the thief can effectively impersonate as their target for years.
How do I know if my identity has been stolen?
The earlier you recognize the warning indicators of identity theft, the more cautious you should be. Maintaining a tight eye on your credit card records and bank accounts can put you in a better position to identify any unusual activity as soon as it occurs.
Keep an eye out for the following identity theft warning signs:
- Unusual behavior on your bank statements. Any transactions or purchases that you did not make yourself may be signs of identity theft. This also applies to any new loan applications that appear on your credit record. Always get in touch with your financial providers right away if you see something on your statements that doesn’t seem right.
- Unexpected variations in credit score. When an identity thief gets approved for a loan, your credit score could rise, and if someone is making purchases under your name, it might fall.
- A credit or loan is denied to you. If you are eligible for the loan, a denial could mean that your credit has been abused by identity theft, even if this isn’t always the case.
- There’s no tax refund for you. Your government will inform you that your tax returns have already been filed if an identity thief has falsely claimed them.
- Private information about you is being exploited. In a sneaky tactic known as “doxxing,” identity thieves may obtain your personal information and threaten to publicize it or use it as leverage against you.
- There is a debt collector pursuing you. You can start receiving notifications from collection agencies when identity thieves spend an increasing amount of money using your name.
- warnings for unidentified logins. Many websites notify you when you use a new device to connect into your account. However, failing to do so may indicate that your credentials have been obtained by someone else.
- unfamiliar medical documentation. Theft of a medical identity may lead to the addition of the criminal’s medical history to yours. Watch out for unexplained medical procedures or conditions, and be cautious when reading insurance records that list unreceived medical treatments.
What to do if you’re a victim of identity theft
Have you observed any of the warning indicators listed above? You can take immediate action if you suspect that you may be a target of essence theft. Don’t panic. And never forget that you have company. Every year, fraud and identity theft impact a great number of people worldwide. Your chances of fully recovering from identity theft are higher the sooner you report it.
Reporting any warning indications to the appropriate organizations right away is the first thing you should do. For instance, get in touch with your credit card company and let them know about any strange expenditures you’re noticing on your statement. They are aware of what to do.
Next, if you can, freeze your credit in addition to all of your other accounts. By doing this, an identity thief will be prevented from doing more harm. Cybercrimes should always be reported to the appropriate government agency or entity in your nation. It’s critical to keep in mind that fraud and identity theft are types of cybercrimes.
Now that you’ve turned in all of your reports, it’s time to stop identity theft from happening again. Consequently, change all of your passwords, being sure to use strong, one-of-a-kind passwords for each account. In addition, you might need to amend any personal information that was impacted by identity theft, such your criminal or medical background, or replace any legal papers.
How to protect yourself against identity theft
Targets that are most susceptible to attack are the ones that identity thieves will always pursue. Because of this, it’s crucial to fortify yourself against identity theft by making a few simple adjustments to your digital lifestyle.
- Make distinct passwords. This advice is so important that we have discussed it numerous times in this post. A thief will only be able to access that one account if they manage to get their hands on one of your passwords.
- Keep an eye on your documentation. The best method for apprehending an identity thief is this. Examine your credit card statements, bank statements, health insurance records, and other documents carefully at all times.
- Make use of two-factor authentication. As soon as you can, turn on two-factor authentication (2FA). Although it’s not impenetrable, it makes it much more difficult to access your account.
- Shut off your phone. A password, PIN, or fingerprint lock will deter criminals if you misplace your phone. However, before turning on facial recognition, give it some thought. It makes it simple for someone to unlock your phone by just pointing it at you.
- Reduce the amount of social media sharing. By limiting the information you disclose online, identity thieves will have less information about you to work with.
- Frozen credit should be kept until needed. When you require a loan, unfreeze your credit, and as soon as you’re through, freeze it.
- Make use of a VPN. Employ a VPN to encrypt your internet association to keep nimble hackers from stealing your information while you browse. This is especially crucial if you use public WiFi.
- Acknowledge the signs of pharming and phishing assaults. Before interacting with emails or visiting websites, never submit personal information, download anything, or click any links.
- Make use of antivirus software. The greatest antiviral programs shield users from viruses as well. It also protects you from harmful websites and phishing assaults.
Keep close tabs on your personal data with avast
Although fighting identity theft is never too late, the greatest defense is always prevention. An integrated identity theft monitoring function in Avast One looks for any evidence of your personal information through data breaches. Avast One will assist you in locking down your accounts in the event that your information is ever discovered to have been compromised, preventing identity theft.
Additionally, Avast will assist you in handling the aftermath and safeguarding your credentials in the terrible event that your data is compromised. You are the only one who need access to your financial accounts. Use Avast One to keep everyone else out.